Detect email abuse using DMARC reports
With DMARC, you can specify a destination for reports on e-mails (claiming to come) from your domain. This also allows you to detect when a malicious script on one or more of your own servers is sending unsolicited emails.

DMARC allows you to specify a destination for aggregate (rua) and failure (ruf) reports regarding emails (that claim to be) from your domain. This also allows you to detect when a malicious script on one or more of your servers sends unsolicited emails.
Last week, we saw a massive increase in aggregate and failure reports for one of our users. We informed the user, and after we'd resolved the problem, they kindly allowed us to use their anonymized data to show others how to detect and resolve this type of abuse.
DMARC aggregate
When a malicious script sends (vast amounts of) emails, the biggest problem is that SPF will not fail because the email originates from your server(s). If messages are sent through your MTA, the email is probably also signed with DKIM. Because both SPF and DKIM will align, the receiving mail servers will not reject the messages based on the DMARC policy.
The first thing you will probably notice is the massive increase in the number of reports you receive. For example, if your domain typically sends about 100 emails a day, and suddenly you receive reports for more than 190,000 emails, you are likely to have a problem.
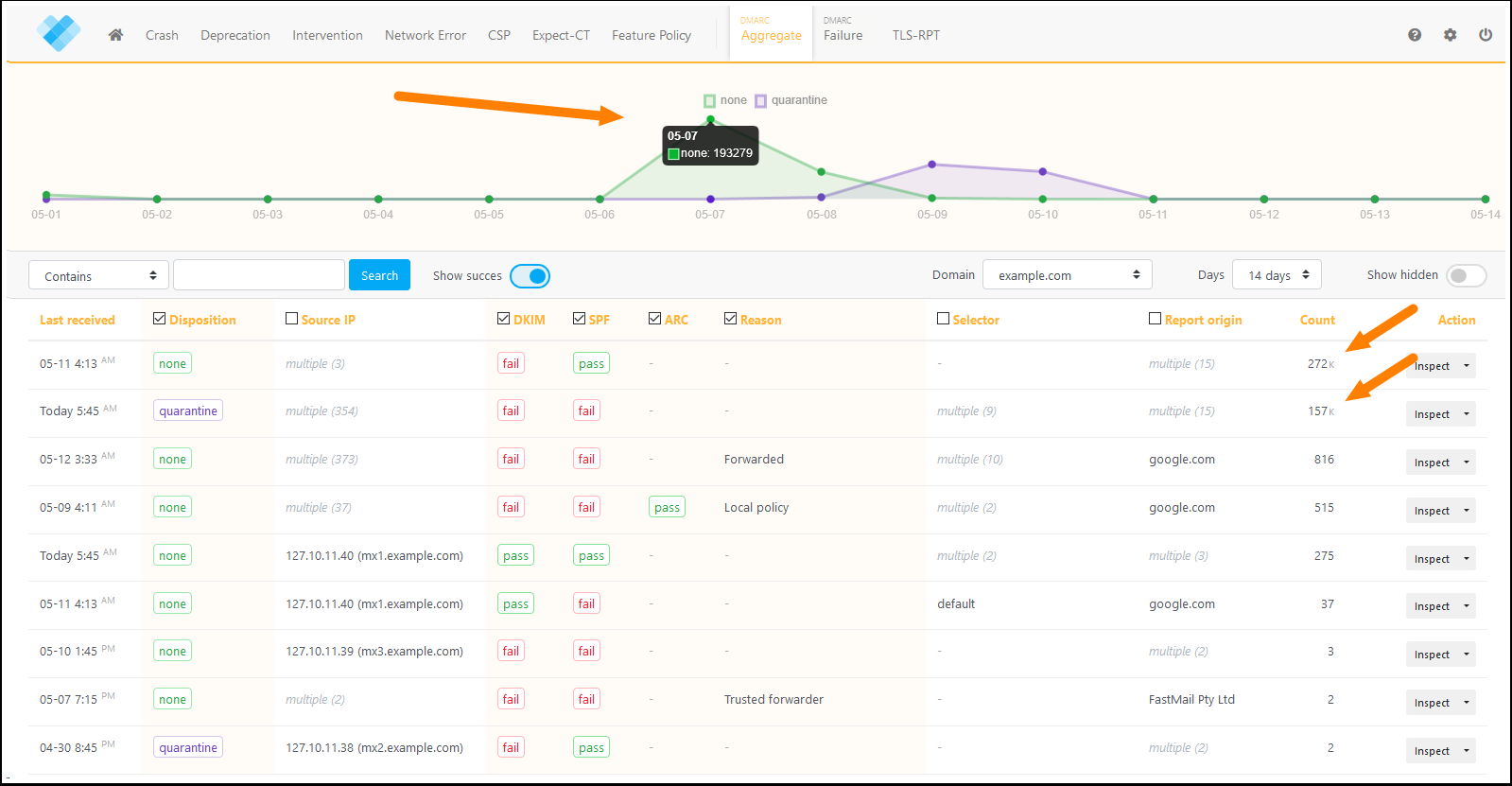
Have a look at the reports above. You can probably guess when the malicious script started sending emails.
DMARC failure
As soon as receiving servers quarantine or reject the messages, the failure reports will start flooding in. These reports contain more valuable information, such as the name of the sender, the email subject, and the message headers.
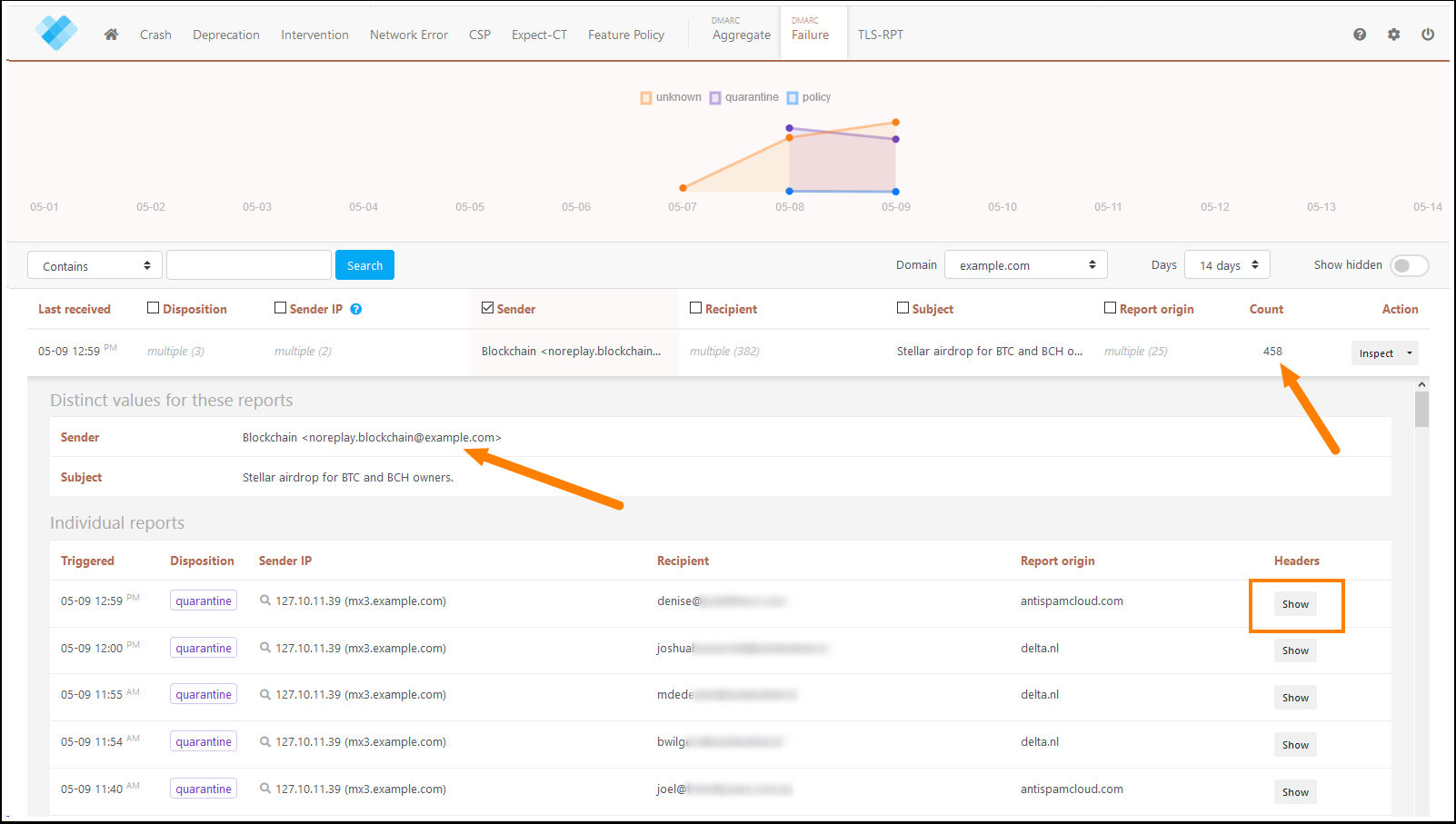
The message headers may contain data that can lead you to the correct server and even the exact filename responsible for sending the message. This allows you to detect and remove the cause and prevent more emails from being sent.
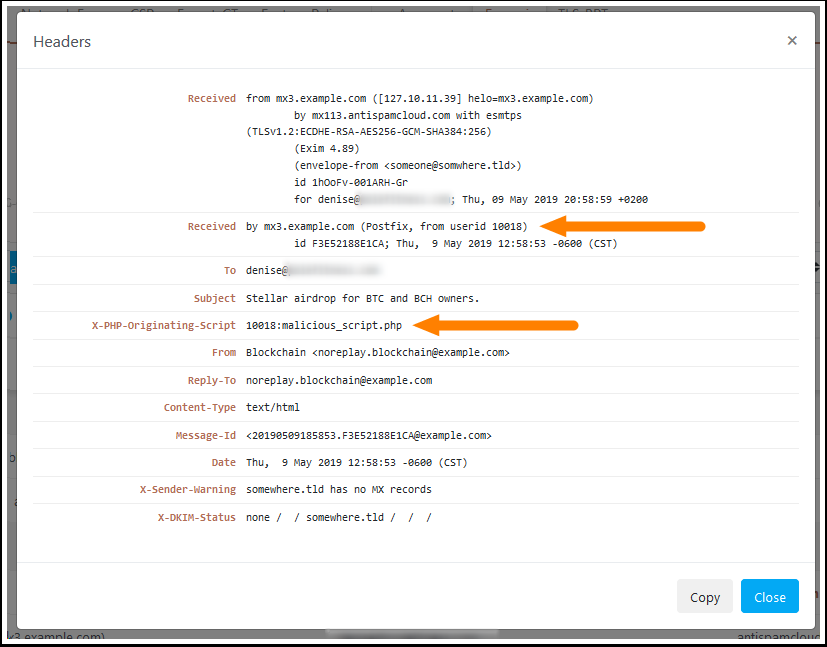
As you can see, URIports helps you to detect and solve all kinds of problems with your website and email server. So, if you haven't set up SPF, DKIM, and DMARC yet, get right to it. You can read more about email security in my previous blog here.

