Demystifying DMARC Alignment

Introduction
A common challenge for those delving into email security is grasping the concept of alignment in SPF and DKIM. This blog sheds light on what alignment entails and its critical role in ensuring successful DMARC validation.
Authenticated Identifiers
Upon receiving an email, the receiving server validates SPF using the domain specified in the RFC5321.MailFrom address. This address is also referred to as the envelope from:, bounce address, or return path. This address can differ from the RFC5322.From (Header From:) address the recipient sees as the email's sender.
An email may also be authenticated with a DKIM signature. This allows a domain to assert responsibility for the email and ensure it hasn't been altered in transit. The domain verified by DKIM (d= value in the DKIM-Signature: header) can also differ from the RFC5322.From address the recipient sees as the email's sender.
This discrepancy can create a security loophole, where an email, though validated and authenticated by SPF and DKIM, might claim to be from somebody completely different.
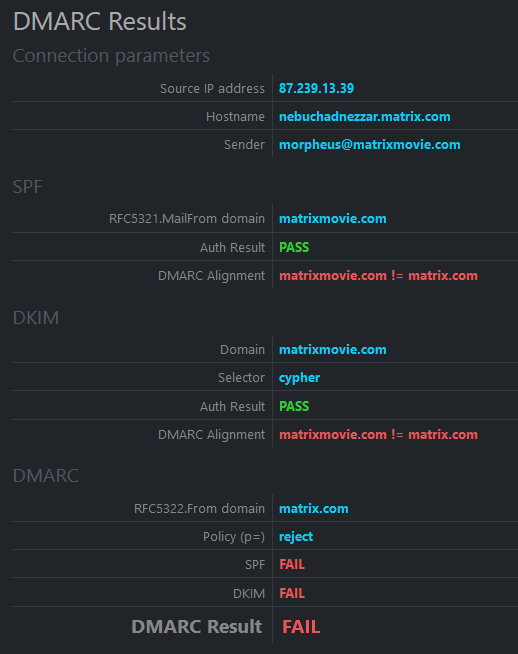
Introducing DMARC
DMARC effectively bridges these gaps. While DMARC is commonly associated with report generation, DMARC's key role is in checking the alignment of the authenticated identifiers mentioned above with the RFC5322.From address.
For DMARC to pass, it's not just about having SPF or DKIM validation succeed; at least one must generate a pass AND align with the RFC5322.From address.
Strict vs. Relaxed
DMARC's default setting is relaxed alignment, where alignment is achieved as long as the organizational domains match. Changing the aspf or adkim elements in the DMARC policy to s (strict) requires a complete hostname match.
See alignment in action
For a visual understanding of SPF, DKIM, and DMARC, including alignment, visit learnDMARC.com. Use the "load random example" button to see instances of emails failing or passing the alignment test.
More info?
Here are more links with information about SPF, DKIM, and DMARC:
Introduction to SPF, DKIM, and DMARC
Email Security Explained
SPF, DKIM, and DMARC Best Practices

